
In my line of work I am exposed to various Wordpress installations – different plug-in sets, different themes, various amount of content – so, I have my fair share of troubleshooting Wordpress performance issues related to almost anything.
Read more »
Author Archives: admin - Page 5
Wordpress: how to trim your wp_options table
Centos: How to configure DKIM for sendmail on multiple domains
 I wanted to configure DKIM for sendmail on multiple domains for one of the dedicated servers and found out that there are no usable instructions for CentOS and few that are available are inconclusive (I will provide the list of information sources at the end of this post). Here is my tested working setup:
I wanted to configure DKIM for sendmail on multiple domains for one of the dedicated servers and found out that there are no usable instructions for CentOS and few that are available are inconclusive (I will provide the list of information sources at the end of this post). Here is my tested working setup:
Read more »
Sysadmin: Why CentOS?
![]() Why CentOS as our main server farm Linux distribution? I really want this article to be pure technical, but there are some emotions attached to the question so please forgive me if I might break into rant somewhere down the road.
Why CentOS as our main server farm Linux distribution? I really want this article to be pure technical, but there are some emotions attached to the question so please forgive me if I might break into rant somewhere down the road.
There were so many times when I was asked by young men with bright eyes and too much free time on their hands “Why do you use Centos for your server farm? Why not (debian,ubuntu, gentoo, insert your favorite distribution here)?” And I am so tired of explaining this decision over and over so I decided to put it together in this article and get it over with once and for all.
Read more »
Prepaid mobile data in Greece: 3Gb for 15euro
 Prepaid mobile data plan in Greece from Wind is definitely worth to consider if you are travelling there and need to be online while on the move.
Prepaid mobile data plan in Greece from Wind is definitely worth to consider if you are travelling there and need to be online while on the move.
Read more »
Sysadmin: How to protect WordPress against “POST /wp-login.php” attacks
 During last few weeks I’ve witnessed repeated semi-successful attacks against WordPress sites. This attack is easy to recognize – server response is extremely slow and if you take a look at apache ‘server-status’ page you will see multiple ‘POST /wp-login.php’ requests from different IPs.
During last few weeks I’ve witnessed repeated semi-successful attacks against WordPress sites. This attack is easy to recognize – server response is extremely slow and if you take a look at apache ‘server-status’ page you will see multiple ‘POST /wp-login.php’ requests from different IPs.
Read more »
Sysadmin: block these pesky recursive DNS queries with iptables rate limiting rules
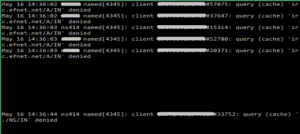 If you are managing Linux server you have probably heard about recent DNS amplification attacks that were using misconfigured DNS servers.
If you are managing Linux server you have probably heard about recent DNS amplification attacks that were using misconfigured DNS servers.
Read more »
Centos: How to run additional apache instance on different port
In some situations you might need to configure and run additional apache httpd instance listening on different port. It is really easy to accomplish using minimal modifications to the standard CentOS apache httpd configuration and init script.
Read more »
sysadmin: Brute Force Detection – first line of defense
Most of the hosting servers nowadays are plagued by brute force attacks – too many computers running some or other botnet, too many “no brainer” scan tools are available for the interested.
There are always somebody who doesn’t bother to select good password to secure his account on the server and that could potentially bring a lot of problems not only to him but to the whole hosting company as well – imagine brute-forced password used for SMTP AUTH to send massive amounts of SPAM from the compromised server?
Now there is lot of countermeasures invented for that and here I will explain which one I prefer and why.
Read more »
Rant: Keep your critical data local
I think it’s about time I’ll add some personal rant to this blog to add some personal touch to it. Just few words about critical data storage at modern times.
I had a customer server disk failure the other day. Nothing extraordinary about that – old server circa 2006 or 2008 happily humming on old IDE western digital’s 160Gb softraid mirror.
Read more »
Sysadmin: correcting file permissions recursively from the shell
In a way of troubleshooting web application there is the step when all known reasons why it doesn’t work exhausted so they just change permissions on everything to 0777 and hope that this drastic step would fix the problem. Most likely it does not but leaves the permissions broken and and the whole site wide open.
Usually nobody cares until first break-in, then everybody start looking for the responsible parties, and host is first and most likely last to blame.
In order to avoid this problem permissions (and possibly ownership) of the web content should be corrected.
Read more »