I’ve hit an unusual error the other day – I had to configure couple of SSL virtual hosts on Nginx web server. I didn’t expect to see any problems with that – it’s really simple and very well documented. The purpose was to switch Cloudflare CDN crypto option from “Flexible” to “Full”, to avoid unencrypted connection between Cloudflare and the server itself. The tricky part is that you have to have SSL virtual host configured on the server side before doing redirection otherwise you will get redirect loop.
I configured both of the SSL virtual hosts (thought second virtual host with ssl_certificate and ssl_certificate_key commented out) and tried to modify Cloudflare configuration – and then I’ve got 525 protocol error. I turned off the caching and tried to investigate.
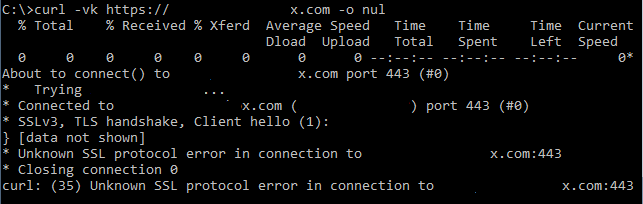
I tried to use OpenSSL to troubleshoot SSL connection with “s_client” option, trying to connect to each SSL virtual host directly, bypassing Cloudflare and I saw an interesting picture
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
C:\>\openssl.exe s_client -connect vhost.com:443 Loading 'screen' into random state - done CONNECTED(00000190) 16220:error:140790E5:SSL routines:SSL23_WRITE:ssl handshake failure:.\ssl\s23_li b.c:177: --- no peer certificate available --- No client certificate CA names sent --- SSL handshake has read 0 bytes and written 210 bytes --- New, (NONE), Cipher is (NONE) Secure Renegotiation IS NOT supported Compression: NONE Expansion: NONE --- |
and more verbosely
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 |
C:\>\openssl.exe s_client -debug -connect vhost.com:443 Loading 'screen' into random state - done CONNECTED(00000190) write to 0x38d670 [0x7a5ea8] (210 bytes => 210 (0xD2)) 0000 - 16 03 01 00 cd 01 00 00-c9 03 01 58 b4 d9 62 af ...........X..b. 0010 - c4 ea 07 a4 a9 ba 2f d9-b4 50 f3 3f 2a 05 89 71 ....../..P.?*..q 0020 - 9b de 7f 70 48 13 fb 0d-e8 88 8c 00 00 5c c0 14 ...pH........\.. 0030 - c0 0a 00 39 00 38 00 88-00 87 c0 0f c0 05 00 35 ...9.8.........5 0040 - 00 84 c0 12 c0 08 00 16-00 13 c0 0d c0 03 00 0a ................ 0050 - c0 13 c0 09 00 33 00 32-00 9a 00 99 00 45 00 44 .....3.2.....E.D 0060 - c0 0e c0 04 00 2f 00 96-00 41 00 07 c0 11 c0 07 ...../...A...... 0070 - c0 0c c0 02 00 05 00 04-00 15 00 12 00 09 00 14 ................ 0080 - 00 11 00 08 00 06 00 03-00 ff 01 00 00 44 00 0b .............D.. 0090 - 00 04 03 00 01 02 00 0a-00 34 00 32 00 01 00 02 .........4.2.... 00a0 - 00 03 00 04 00 05 00 06-00 07 00 08 00 09 00 0a ................ 00b0 - 00 0b 00 0c 00 0d 00 0e-00 0f 00 10 00 11 00 12 ................ 00c0 - 00 13 00 14 00 15 00 16-00 17 00 18 00 19 00 23 ...............# 00d2 - <SPACES/NULS> read from 0x38d670 [0x7ab408] (7 bytes => 0 (0x0)) 4372:error:140790E5:SSL routines:SSL23_WRITE:ssl handshake failure:.\ssl\s23_lib .c:177: --- no peer certificate available --- No client certificate CA names sent --- SSL handshake has read 0 bytes and written 210 bytes --- New, (NONE), Cipher is (NONE) Secure Renegotiation IS NOT supported Compression: NONE Expansion: NONE --- |
And then it hit me – I’ve turned on SSL mode on the virtual host and not specified nor certificate no key, then I’ve configured another SSL virtual host with valid certificate and key configured but the SSL is running on the single IP so it’s in SNI mode, sends me an EMPTY SSL SNI negotiation start. In order to avoid the problem I need to have valid certificates for ALL my SNI SSL virtual hosts. After I altered my configuration the problem was fixed.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 |
C:\>\openssl.exe s_client -connect vhost.com: 443 Loading 'screen' into random state - done CONNECTED(00000190) depth=0 C = FR, ST = Paris, L = Paris, O = Default Company Ltd, CN = localhost verify error:num=18:self signed certificate verify return:1 depth=0 C = FR, ST = Paris, L = Paris, O = Default Company Ltd, CN = localhost verify return:1 --- Certificate chain 0 s:/C=FR/ST=Paris/L=Paris/O=Default Company Ltd/CN=localhost i:/C=FR/ST=Paris/L=Paris/O=Default Company Ltd/CN=localhost --- Server certificate -----BEGIN CERTIFICATE----- MIIDkTCCAnmgAwIBAgIJAOAnX6QNo1rxMA0GCSqGSIb3DQEBCwUAMF8xCzAJBgNV BAYTAkZSMQ4wDAYDVQQIDAVQYXJpczEOMAwGA1UEBwwFUGFyaXMxHDAaBgNVBAoM E0RlZmF1bHQgQ29tcGFueSBMdGQxEjAQBgNVBAMMCWxvY2FsaG9zdDAeFw0xNzAy MjcxNTMxNDhaFw0yNzAyMjUxNTMxNDhaMF8xCzAJBgNVBAYTAkZSMQ4wDAYDVQQI DAVQYXJpczEOMAwGA1UEBwwFUGFyaXMxHDAaBgNVBAoME0RlZmF1bHQgQ29tcGFu eSBMdGQxEjAQBgNVBAMMCWxvY2FsaG9zdDCCASIwDQYJKoZIhvcNAQEBBQADggEP ADCCAQoCggEBAO7bt5v2G3uCouQmWkEawc+E18X3IpQA0+VjS1FoIuClKpgNS7X0 CrPEmQIMTkltsve3a0kPC7UeqMjPObb3wX8i+AvGsoeAXJA4ZQDIiHl4UuqCMLpm F2UKjkLcoxkFlinFq2yYZEk6o9awVKsFY14yN9NUpEIl/daJArtaW/a4B1M8RKRO PqSDFajAGXNUQ59tY+HzKNNRG8+c6Uoq+wTiKvOQYsKkGJysMXMgZ3wrTbWC3pEO FGwWvgjyF1YNWstBPPUZy6nOkQvnw7dkdAr23FA6qfnxhTieF94C2XyI7N5AFtYD 9thJiK+jIYtIQUBiPHHUscpx1agMWXC21jsCAwEAAaNQME4wHQYDVR0OBBYEFPx9 5Wv5QjChS/kCgONa0FcL3ifsMB8GA1UdIwQYMBaAFPx95Wv5QjChS/kCgONa0FcL 3ifsMAwGA1UdEwQFMAMBAf8wDQYJKoZIhvcNAQELBQADggEBAFgdmFU4rg2eDQcC neU7A5iwrbJtK2k6HS987yStA+U09gDwCwsJRGWJ+NFJvqyNW2816VeI2yp2+02P liluMjOIQzC/5UVXrac5DmpDz71LR/x6H9ksYm/28PyTCQmtmz+V8TtM3FdPFe+s hNiO5v7LPed0lRzkYjyyXW17VBlta0EbkIMCDdtCvTnMj7IWeBF+/WwgvRB9at67 DYJv5TP4B7wxi2mahDpOYKyzue3k+OaGMqRJGPdm9RQMID99LUcsSd6m/UCJO8AK VvfYwB6cVCkpVIDx4kiZtkKBw/Vgts39d9aJ/tPOGZexwdK6T4yXZ8CPTHGNCO24 V4oznag= -----END CERTIFICATE----- subject=/C=FR/ST=Paris/L=Paris/O=Default Company Ltd/CN=localhost issuer=/C=FR/ST=Paris/L=Paris/O=Default Company Ltd/CN=localhost --- No client certificate CA names sent --- SSL handshake has read 1593 bytes and written 344 bytes --- |