
Last week I had really hard time dealing with the server that was hit by multiple Wordpress vulnerabilities in a row. Not to mention some outdated versions and cpanel account password leakage because of the server owner. During the long hours I’ve devised more or less effective procedure for cleaningup compromised Wordpress sites that’s proven relatively effective, given the circumstances. The precondition is that that I don’t have any access to the site backup, and didn’t have much time to examine particular theme or plugin (oh there were few custom built and long discontinued plugins that I had to preserve). So, to the business at hand.
Read more »
Category Archives: Security
Sysadmin: How to cleanup compromised Wordpress site
How to make older Android devices work with Letsencrypt ROOT certificate

The most impacting technical event of the Internet was the expiration of the Letsencrypt DST Root certificate which brought a lot of grief to technical support people and owners of declared obsolete devices. Here is the lists of compatible and incompatible devices provided by Letsencrypt.
There is a way to make some of incompatible devices work, by manually installing ISRG Root X1 Letsencrypt certificate, here is brief instruction for older Apple OS, and below I will show how to do the same on Android 6.0.1 phone.
Read more »
Windows: What do I want to see as default browser

Why Did I bother with it at all?
As I wrote before it is more convenient and secure to have something small, fast and feature limited as your default browser (valid decision for all OSes out there).
Well times go by and nice small Qtweb got outdated with development on it stopped about 6 years ago and new standards (namely SSL/TLS) and new vulnerabilities came out, so I decided
Read more »
Sysadmin: Letsencrypt renewal htaccess redirect bypass
With increasing role of HTTPS websites (Google pushing everybody to run only HTTPS websites considering regular HTTP as insecure) the service provided by Let’s encrypt becomes critically important. But there is a catch – once you get the certificate and redirect your site to HTTPS using .htaccess you will get a problem renewing certificate because 301 redirect breaks the challenge verification and the command
|
1 |
certbot-auto renew |
gives an error about authorization problem.
Read more »
Sysadmin: Virtualmin and Letsencrypt integration


If you are using webmin excellent system for managing virtual host configuration it would make perfect sense to integrate with it the popular certificate authority Letsencrypt that issues completely free SSL certificates.
There are few initial steps that has to be made nside Webmin in order to make it utilize Letsencrypt SSL certificate issuing process for configured virtual hosts. I have successufully configured and used Webmin version 1.831 and certbot-auto 0.12. YMMV.
Read more »
Sysadmin: How to install Letsencrypt on CentOS

Since Letsencrypt started their services life became much easier (or less). You can get free valid and secure SSL certificates that are recognized by majority of browsers, but for that you need to do some initial configuration and keep in mind that if you don’t renew all these nice certificates will turn into pumpkin after 2 month.
Here is the one liner command to install certbot-auto in CentOS 6 (requires additional Python 2.7 from EPEL repo)
|
1 2 3 4 5 6 |
yum -y install python27 python27-devel python27-pip cd /usr/local/sbin wget https://dl.eff.org/certbot-auto chmod +x ./certbot-auto export PYTHON=/usr/bin/python2.7 ./certbot-auto register --agree-tos --no-eff-email -m <your@email.address> |
Almost, the same for the CentOS 7 just without Python.
|
1 2 3 4 |
cd /usr/local/sbin wget https://dl.eff.org/certbot-auto chmod +x ./certbot-auto ./certbot-auto register --agree-tos --no-eff-email -m <your@e-mail.address> |
Here is how quickly request/retrieve certificate for your website on domain.com that is hosted under /home/domain/public_html from command line (presuming that the site is answering on this server already e.g. DNS and web server configured properly)
|
1 2 |
/usr/local/sbin/certbot-auto certonly --webroot \ -w /home/domain/public_html -d domain.com -d www.domain.com |
If the request was successful your new certificates could be accessible from /etc/letsencrypt/live/domain.com, where
privkey.pem – is the certificate key, cert.pem – bare certificate fullchain.pem – certificate along with the whole CA chain.
Don’t forget that these are valid for 2 month only. You’ll need to run
|
1 |
/usr/local/sbin/certbot-auto renew |
after that to get valid certificates.
SSL protocol error 525 for nginx solved
I’ve hit an unusual error the other day – I had to configure couple of SSL virtual hosts on Nginx web server. I didn’t expect to see any problems with that – it’s really simple and very well documented. The purpose was to switch Cloudflare CDN crypto option from “Flexible” to “Full”, to avoid unencrypted connection between Cloudflare and the server itself. The tricky part is that you have to have SSL virtual host configured on the server side before doing redirection otherwise you will get redirect loop.
I configured both of the SSL virtual hosts (thought second virtual host with ssl_certificate and ssl_certificate_key commented out) and tried to modify Cloudflare configuration – and then I’ve got 525 protocol error. I turned off the caching and tried to investigate.
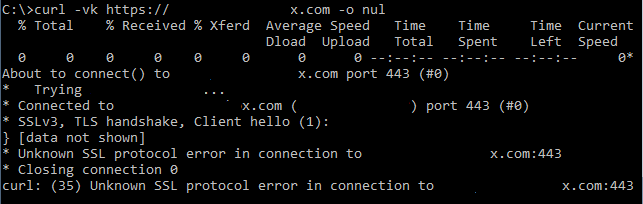
I tried to use OpenSSL to troubleshoot SSL connection with “s_client” option, trying to connect to each SSL virtual host directly, bypassing Cloudflare and I saw an interesting picture
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
C:\>\openssl.exe s_client -connect vhost.com:443 Loading 'screen' into random state - done CONNECTED(00000190) 16220:error:140790E5:SSL routines:SSL23_WRITE:ssl handshake failure:.\ssl\s23_li b.c:177: --- no peer certificate available --- No client certificate CA names sent --- SSL handshake has read 0 bytes and written 210 bytes --- New, (NONE), Cipher is (NONE) Secure Renegotiation IS NOT supported Compression: NONE Expansion: NONE --- |
and more verbosely
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 |
C:\>\openssl.exe s_client -debug -connect vhost.com:443 Loading 'screen' into random state - done CONNECTED(00000190) write to 0x38d670 [0x7a5ea8] (210 bytes => 210 (0xD2)) 0000 - 16 03 01 00 cd 01 00 00-c9 03 01 58 b4 d9 62 af ...........X..b. 0010 - c4 ea 07 a4 a9 ba 2f d9-b4 50 f3 3f 2a 05 89 71 ....../..P.?*..q 0020 - 9b de 7f 70 48 13 fb 0d-e8 88 8c 00 00 5c c0 14 ...pH........\.. 0030 - c0 0a 00 39 00 38 00 88-00 87 c0 0f c0 05 00 35 ...9.8.........5 0040 - 00 84 c0 12 c0 08 00 16-00 13 c0 0d c0 03 00 0a ................ 0050 - c0 13 c0 09 00 33 00 32-00 9a 00 99 00 45 00 44 .....3.2.....E.D 0060 - c0 0e c0 04 00 2f 00 96-00 41 00 07 c0 11 c0 07 ...../...A...... 0070 - c0 0c c0 02 00 05 00 04-00 15 00 12 00 09 00 14 ................ 0080 - 00 11 00 08 00 06 00 03-00 ff 01 00 00 44 00 0b .............D.. 0090 - 00 04 03 00 01 02 00 0a-00 34 00 32 00 01 00 02 .........4.2.... 00a0 - 00 03 00 04 00 05 00 06-00 07 00 08 00 09 00 0a ................ 00b0 - 00 0b 00 0c 00 0d 00 0e-00 0f 00 10 00 11 00 12 ................ 00c0 - 00 13 00 14 00 15 00 16-00 17 00 18 00 19 00 23 ...............# 00d2 - <SPACES/NULS> read from 0x38d670 [0x7ab408] (7 bytes => 0 (0x0)) 4372:error:140790E5:SSL routines:SSL23_WRITE:ssl handshake failure:.\ssl\s23_lib .c:177: --- no peer certificate available --- No client certificate CA names sent --- SSL handshake has read 0 bytes and written 210 bytes --- New, (NONE), Cipher is (NONE) Secure Renegotiation IS NOT supported Compression: NONE Expansion: NONE --- |
And then it hit me – I’ve turned on SSL mode on the virtual host and not specified nor certificate no key, then I’ve configured another SSL virtual host with valid certificate and key configured but the SSL is running on the single IP so it’s in SNI mode, sends me an EMPTY SSL SNI negotiation start. In order to avoid the problem I need to have valid certificates for ALL my SNI SSL virtual hosts. After I altered my configuration the problem was fixed.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 |
C:\>\openssl.exe s_client -connect vhost.com: 443 Loading 'screen' into random state - done CONNECTED(00000190) depth=0 C = FR, ST = Paris, L = Paris, O = Default Company Ltd, CN = localhost verify error:num=18:self signed certificate verify return:1 depth=0 C = FR, ST = Paris, L = Paris, O = Default Company Ltd, CN = localhost verify return:1 --- Certificate chain 0 s:/C=FR/ST=Paris/L=Paris/O=Default Company Ltd/CN=localhost i:/C=FR/ST=Paris/L=Paris/O=Default Company Ltd/CN=localhost --- Server certificate -----BEGIN CERTIFICATE----- MIIDkTCCAnmgAwIBAgIJAOAnX6QNo1rxMA0GCSqGSIb3DQEBCwUAMF8xCzAJBgNV BAYTAkZSMQ4wDAYDVQQIDAVQYXJpczEOMAwGA1UEBwwFUGFyaXMxHDAaBgNVBAoM E0RlZmF1bHQgQ29tcGFueSBMdGQxEjAQBgNVBAMMCWxvY2FsaG9zdDAeFw0xNzAy MjcxNTMxNDhaFw0yNzAyMjUxNTMxNDhaMF8xCzAJBgNVBAYTAkZSMQ4wDAYDVQQI DAVQYXJpczEOMAwGA1UEBwwFUGFyaXMxHDAaBgNVBAoME0RlZmF1bHQgQ29tcGFu eSBMdGQxEjAQBgNVBAMMCWxvY2FsaG9zdDCCASIwDQYJKoZIhvcNAQEBBQADggEP ADCCAQoCggEBAO7bt5v2G3uCouQmWkEawc+E18X3IpQA0+VjS1FoIuClKpgNS7X0 CrPEmQIMTkltsve3a0kPC7UeqMjPObb3wX8i+AvGsoeAXJA4ZQDIiHl4UuqCMLpm F2UKjkLcoxkFlinFq2yYZEk6o9awVKsFY14yN9NUpEIl/daJArtaW/a4B1M8RKRO PqSDFajAGXNUQ59tY+HzKNNRG8+c6Uoq+wTiKvOQYsKkGJysMXMgZ3wrTbWC3pEO FGwWvgjyF1YNWstBPPUZy6nOkQvnw7dkdAr23FA6qfnxhTieF94C2XyI7N5AFtYD 9thJiK+jIYtIQUBiPHHUscpx1agMWXC21jsCAwEAAaNQME4wHQYDVR0OBBYEFPx9 5Wv5QjChS/kCgONa0FcL3ifsMB8GA1UdIwQYMBaAFPx95Wv5QjChS/kCgONa0FcL 3ifsMAwGA1UdEwQFMAMBAf8wDQYJKoZIhvcNAQELBQADggEBAFgdmFU4rg2eDQcC neU7A5iwrbJtK2k6HS987yStA+U09gDwCwsJRGWJ+NFJvqyNW2816VeI2yp2+02P liluMjOIQzC/5UVXrac5DmpDz71LR/x6H9ksYm/28PyTCQmtmz+V8TtM3FdPFe+s hNiO5v7LPed0lRzkYjyyXW17VBlta0EbkIMCDdtCvTnMj7IWeBF+/WwgvRB9at67 DYJv5TP4B7wxi2mahDpOYKyzue3k+OaGMqRJGPdm9RQMID99LUcsSd6m/UCJO8AK VvfYwB6cVCkpVIDx4kiZtkKBw/Vgts39d9aJ/tPOGZexwdK6T4yXZ8CPTHGNCO24 V4oznag= -----END CERTIFICATE----- subject=/C=FR/ST=Paris/L=Paris/O=Default Company Ltd/CN=localhost issuer=/C=FR/ST=Paris/L=Paris/O=Default Company Ltd/CN=localhost --- No client certificate CA names sent --- SSL handshake has read 1593 bytes and written 344 bytes --- |
Centos: How to fine tune your Apache SSL server
The fine tuning of the SSL server side configuration is slow and tedious but necessary procedure. It’s always good to have your SSL site to conform the most latest security standards. It boosts ego and makes customer happy too. It turns out that all you need for that is already at your disposal the point is to properly configure it.
Read more »
Sysadmin: Brute force detection – custom rule for SMTP and SSH
I wrote before about excellent tool BFD that allows to block brute force password guessing attempts on different network services.
I prefer it to Fail2ban because of portability (bash script) system resource consumption (bash script!) and extendаbility (true “unix way” modularity).
I also wrote before a brief instruction on how to extend BFD with your own rule to fight with apache/Wordpress DOS attack.
In this post I will show you how to write custom rules to block SMTP password guessing brute force attempts and SSSHD
Windows: Set lightweight web browser as MS windows default web browser application.
 I was thinking the other day – it’s not really safe to have MS windows default browser set to MS Internet Explorer, so any URL you accidentally click will be open with it. For the work related activity I user portable browsers. But what about everything else – this is not really safe no matter how many MS security updates are published every week.
I was thinking the other day – it’s not really safe to have MS windows default browser set to MS Internet Explorer, so any URL you accidentally click will be open with it. For the work related activity I user portable browsers. But what about everything else – this is not really safe no matter how many MS security updates are published every week.
So, I decided to find something really small and “feature-poor” to assign it to the default browser.
Read more »