
Last week I had really hard time dealing with the server that was hit by multiple Wordpress vulnerabilities in a row. Not to mention some outdated versions and cpanel account password leakage because of the server owner. During the long hours I’ve devised more or less effective procedure for cleaningup compromised Wordpress sites that’s proven relatively effective, given the circumstances. The precondition is that that I don’t have any access to the site backup, and didn’t have much time to examine particular theme or plugin (oh there were few custom built and long discontinued plugins that I had to preserve). So, to the business at hand.
Read more »
Category Archives: webhosting
Sysadmin: How to cleanup compromised Wordpress site
cPanel: How to replicate DNS zones to external Bind server without views



I’ve got a complain from the customer of my recent cPanel server installation that his DNS zones are not replicated by our main DNS servers and therefore they have problems.
Centos7: “ldconfig : Aborted” error and how to deal with it

On one of my recently installed servers I’ve got customer complain about ffmpeg missing some obscure shared libraries. I went to investigate and met some interesting case
Read more »
Sysadmin: Letsencrypt renewal htaccess redirect bypass
With increasing role of HTTPS websites (Google pushing everybody to run only HTTPS websites considering regular HTTP as insecure) the service provided by Let’s encrypt becomes critically important. But there is a catch – once you get the certificate and redirect your site to HTTPS using .htaccess you will get a problem renewing certificate because 301 redirect breaks the challenge verification and the command
|
1 |
certbot-auto renew |
gives an error about authorization problem.
Read more »
Sysadmin: Virtualmin and Letsencrypt integration


If you are using webmin excellent system for managing virtual host configuration it would make perfect sense to integrate with it the popular certificate authority Letsencrypt that issues completely free SSL certificates.
There are few initial steps that has to be made nside Webmin in order to make it utilize Letsencrypt SSL certificate issuing process for configured virtual hosts. I have successufully configured and used Webmin version 1.831 and certbot-auto 0.12. YMMV.
Read more »
Sysadmin: PHP-FPM modular config

When you have multilple PHP-FPM pools configured on the server you usually store the configurations under /etc/php-fpm.d. When you have a lot of sites this directory starts looking pretty crowded.
Although when you look inside the typical PHP-FPM pool configuration file you can easily notice that there about only 4 lines that make a difference – everything else is absolutely identical.
Read more »
Sysadmin: How to install Letsencrypt on CentOS

Since Letsencrypt started their services life became much easier (or less). You can get free valid and secure SSL certificates that are recognized by majority of browsers, but for that you need to do some initial configuration and keep in mind that if you don’t renew all these nice certificates will turn into pumpkin after 2 month.
Here is the one liner command to install certbot-auto in CentOS 6 (requires additional Python 2.7 from EPEL repo)
|
1 2 3 4 5 6 |
yum -y install python27 python27-devel python27-pip cd /usr/local/sbin wget https://dl.eff.org/certbot-auto chmod +x ./certbot-auto export PYTHON=/usr/bin/python2.7 ./certbot-auto register --agree-tos --no-eff-email -m <your@email.address> |
Almost, the same for the CentOS 7 just without Python.
|
1 2 3 4 |
cd /usr/local/sbin wget https://dl.eff.org/certbot-auto chmod +x ./certbot-auto ./certbot-auto register --agree-tos --no-eff-email -m <your@e-mail.address> |
Here is how quickly request/retrieve certificate for your website on domain.com that is hosted under /home/domain/public_html from command line (presuming that the site is answering on this server already e.g. DNS and web server configured properly)
|
1 2 |
/usr/local/sbin/certbot-auto certonly --webroot \ -w /home/domain/public_html -d domain.com -d www.domain.com |
If the request was successful your new certificates could be accessible from /etc/letsencrypt/live/domain.com, where
privkey.pem – is the certificate key, cert.pem – bare certificate fullchain.pem – certificate along with the whole CA chain.
Don’t forget that these are valid for 2 month only. You’ll need to run
|
1 |
/usr/local/sbin/certbot-auto renew |
after that to get valid certificates.
Sysadmin: how to test your web site before switching DNS
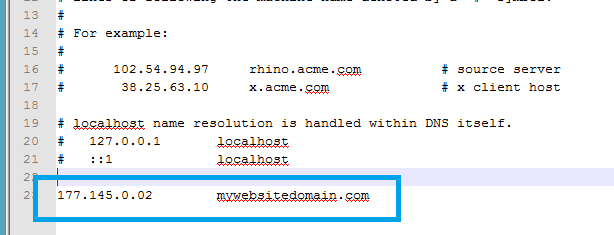 How to test your web site after moving it to the new location, before switching DNS and “going live” there? This situation happens every day, even multiple times a day with single page placeholder sites and huge complicated web portals. I thought I’ll just put together simple instruction to refer people to it instead of explaining it over and over every time.
How to test your web site after moving it to the new location, before switching DNS and “going live” there? This situation happens every day, even multiple times a day with single page placeholder sites and huge complicated web portals. I thought I’ll just put together simple instruction to refer people to it instead of explaining it over and over every time.
So, in order to test your web site on the new server, before switching DNS settings to the new location you will need to fool your desktop browser to look into new IP location. Here is how to do it.
Read more »
Sysadmin: check massive list of urls for HTTP status code reply in single line
As I mentioned in previous post I did a few upgrades to EasyApache4 on couple of WHM/cPanel servers recently. While providing with an impressive list of advantages this upgrade could render some of the hosted sites offline because of missing PHP modules and incompatible PHP versions. In order to minimize the downtime all hosted sites has to be verified for availability. There could be easily hundreds of web sites hosted on single WHM/cPanel server and checking all of them manually will take a lot of time. In Linux almost anything could be automated.
Read more »
cPanel: Upgrade to EasyApache4 important points to consider

So, you also decided to take a leap? It’s about time – a lot of new features are coming with EasyApache4 but in order to reduce downtime one has to be careful in the process.
I’ve done a couple upgrades of a company cPanel servers to EasyApache4 recently – not so easy procedure after all although definitely an improvement to the whole cPanel/WHM ecosystem.
Read more »