 I wanted to configure DKIM for sendmail on multiple domains for one of the dedicated servers and found out that there are no usable instructions for CentOS and few that are available are inconclusive (I will provide the list of information sources at the end of this post). Here is my tested working setup:
I wanted to configure DKIM for sendmail on multiple domains for one of the dedicated servers and found out that there are no usable instructions for CentOS and few that are available are inconclusive (I will provide the list of information sources at the end of this post). Here is my tested working setup:
Read more »
Category Archives: network - Page 2
Centos: How to configure DKIM for sendmail on multiple domains
Sysadmin: block these pesky recursive DNS queries with iptables rate limiting rules
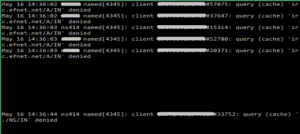 If you are managing Linux server you have probably heard about recent DNS amplification attacks that were using misconfigured DNS servers.
If you are managing Linux server you have probably heard about recent DNS amplification attacks that were using misconfigured DNS servers.
Read more »
Centos: How to run additional apache instance on different port
In some situations you might need to configure and run additional apache httpd instance listening on different port. It is really easy to accomplish using minimal modifications to the standard CentOS apache httpd configuration and init script.
Read more »
sysadmin: Brute Force Detection – first line of defense
Most of the hosting servers nowadays are plagued by brute force attacks – too many computers running some or other botnet, too many “no brainer” scan tools are available for the interested.
There are always somebody who doesn’t bother to select good password to secure his account on the server and that could potentially bring a lot of problems not only to him but to the whole hosting company as well – imagine brute-forced password used for SMTP AUTH to send massive amounts of SPAM from the compromised server?
Now there is lot of countermeasures invented for that and here I will explain which one I prefer and why.
Read more »
Hosting: Howto redirect domain to another domain.
There is always a question on how to completely redirect some src-domain to another dst-domain properly.
And while there is the simple straightforward way to do so, there are always some dedicated server customers of the web hosting that are trying to reinvent the wheel one more time. And failing miserably.
Read more »
Using lsof to find trojan processes on Linux.
In my previous post I was telling about checking for programs using network on Linux using lsof tool.
Here I have “live” example of such backdoor found on one of our servers.
Read more »