 SPAM e-mail is the common problem these days and in most cases the cause of this problem is the lack of security on the hosted web sites. Various badly designed PHP scripts expose the hosting server MTA to be used as SPAM e-mails source. First and foremost step in resolving this problem would be to determine the originating PHP script that was used to send e-mails.
SPAM e-mail is the common problem these days and in most cases the cause of this problem is the lack of security on the hosted web sites. Various badly designed PHP scripts expose the hosting server MTA to be used as SPAM e-mails source. First and foremost step in resolving this problem would be to determine the originating PHP script that was used to send e-mails.
Read more »
Category Archives: Security - Page 2
Sysadmin: How to see the name of PHP script that sent that e-mail
Sysadmin: “[warn-phpd] mmap cache can’t open file … ” mystery solved

Yesterday I was asked by one of our old customers to help solving very interesting problem – he put some php files outside of apache DocumentRoot on his server and the apache could not access the files, producing very interesting lines into apache default error_log
|
1 |
"[warn-phpd] mmap cache can't open file /home/conf.php - permission denied (pid XXX of XXX)" |
How to use BFD tool to block WordPress brute force attacks
I have written about the excellent and lightweight (unlike fail2ban which is more popular but too resource consuming and 3rd party tools dependent) tool BFD earlier. This tool is actually the set of bash scripts that looks for known pattern in the logs and executes actions against offending IPs based on the configuration. Little is known that it’s also modular and allows to extend it’s behavior by writing custom rules to assist with more uncommon situations.
I’ve also written about widespread WordPress brute force attacks that targets wp-logon.php script. The solution I’ve offered there takes care of single WordPress site. It’s getting more difficult to mitigate the attack in case you have multiple servers with multiple WordPress sites. So I decided to come up with more general approach.
Rant: Why I would never have facebook account
 First of all – this is my opinion, it’s emotional, biased, personal and has nothing to do with you. If you are offended by my opinion – you are not required to read, agree with it or argue with me.
First of all – this is my opinion, it’s emotional, biased, personal and has nothing to do with you. If you are offended by my opinion – you are not required to read, agree with it or argue with me.
Read more »
Centos: How to configure DKIM for sendmail on multiple domains
 I wanted to configure DKIM for sendmail on multiple domains for one of the dedicated servers and found out that there are no usable instructions for CentOS and few that are available are inconclusive (I will provide the list of information sources at the end of this post). Here is my tested working setup:
I wanted to configure DKIM for sendmail on multiple domains for one of the dedicated servers and found out that there are no usable instructions for CentOS and few that are available are inconclusive (I will provide the list of information sources at the end of this post). Here is my tested working setup:
Read more »
Sysadmin: How to protect WordPress against “POST /wp-login.php” attacks
 During last few weeks I’ve witnessed repeated semi-successful attacks against WordPress sites. This attack is easy to recognize – server response is extremely slow and if you take a look at apache ‘server-status’ page you will see multiple ‘POST /wp-login.php’ requests from different IPs.
During last few weeks I’ve witnessed repeated semi-successful attacks against WordPress sites. This attack is easy to recognize – server response is extremely slow and if you take a look at apache ‘server-status’ page you will see multiple ‘POST /wp-login.php’ requests from different IPs.
Read more »
Sysadmin: block these pesky recursive DNS queries with iptables rate limiting rules
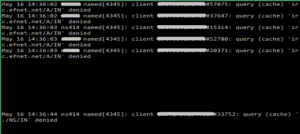 If you are managing Linux server you have probably heard about recent DNS amplification attacks that were using misconfigured DNS servers.
If you are managing Linux server you have probably heard about recent DNS amplification attacks that were using misconfigured DNS servers.
Read more »
sysadmin: Brute Force Detection – first line of defense
Most of the hosting servers nowadays are plagued by brute force attacks – too many computers running some or other botnet, too many “no brainer” scan tools are available for the interested.
There are always somebody who doesn’t bother to select good password to secure his account on the server and that could potentially bring a lot of problems not only to him but to the whole hosting company as well – imagine brute-forced password used for SMTP AUTH to send massive amounts of SPAM from the compromised server?
Now there is lot of countermeasures invented for that and here I will explain which one I prefer and why.
Read more »
Sysadmin: correcting file permissions recursively from the shell
In a way of troubleshooting web application there is the step when all known reasons why it doesn’t work exhausted so they just change permissions on everything to 0777 and hope that this drastic step would fix the problem. Most likely it does not but leaves the permissions broken and and the whole site wide open.
Usually nobody cares until first break-in, then everybody start looking for the responsible parties, and host is first and most likely last to blame.
In order to avoid this problem permissions (and possibly ownership) of the web content should be corrected.
Read more »
Apache, PHP, SuEXEC: added security and control

As we know from original article using Apache, PHP in CGI mode along with suExec gives us 2 important security advantages:
– suExec allows to run PHP process with (only) the file owner user privileges, enforcing proper permissions on PHP scripts and thus allowing to avoid cross-site exploits on the server that is running multiple dynamic web sites;
– per site php.ini.
That gives some unique opportunities for securing separate web sites on the server.
Read more »