 If you are managing Linux server you have probably heard about recent DNS amplification attacks that were using misconfigured DNS servers.
If you are managing Linux server you have probably heard about recent DNS amplification attacks that were using misconfigured DNS servers.
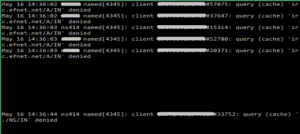
Your server were not misconfigured and still you see a lot of denied queries in your /var/log/messages where somebody is trying to use your DNS server to flood somebody else. In this case it will be “denied” packet and it will still go to the flood target, not to mention flooding your syslog messages log and steal bandwidth from your server.
I’ve found some working solution of this problem on the Internet and put together small shell script to test and use it
|
1 2 3 4 5 6 7 |
#!/bin/bash iptables -F iptables -A INPUT -p udp -m udp --dport 53 -m string --from 50 --algo bm --hex-string '|0000FF0001|' -m recent --set --name dnsanyquery --rsource iptables -A INPUT -p udp -m udp --dport 53 -m string --from 50 --algo bm --hex-string "|0000FF0001|" -m recent --name dnsanyquery --rcheck --seconds 10 --hitcount 1 -j DROP |
There is a room for adjustment for you particular case – seconds is the measurement interval and hitcount – number of queries you allow to reach your server – all other packets from IPs that are over the threshold will be dropped.
I’ve found 1 packet in 10 seconds sufficient to cover most cases.
If you want to have this rules installed on system boot you will need to consult your Linux distro documentation.
For Centos/RHEL it’s relatively easy:
root# iptables-save > /etc/sysconfig/iptables
cant see anything after –hex-strin, for some reason it cant be scrolled
Thank you for noticing it – it should be ok now, looks like html minify broke the css.
This solution does not work. queries still come trough.
It does not block all requests – just reduces the number of recursive requests. Use tcpdump to see what kind of requests are getting. Put allow-recursion {localnets; }; into your named.conf options section too.